Unless you’re living under a rock, you’re familiar with the global IT outage that rocked the world on Friday, July 19th, conveniently before the weekend. The incident spawned from a CrowdStrike update sent to an estimated 8.5 million Windows devices worldwide, which, despite the chaos, is only less than 1% of all Windows machines.
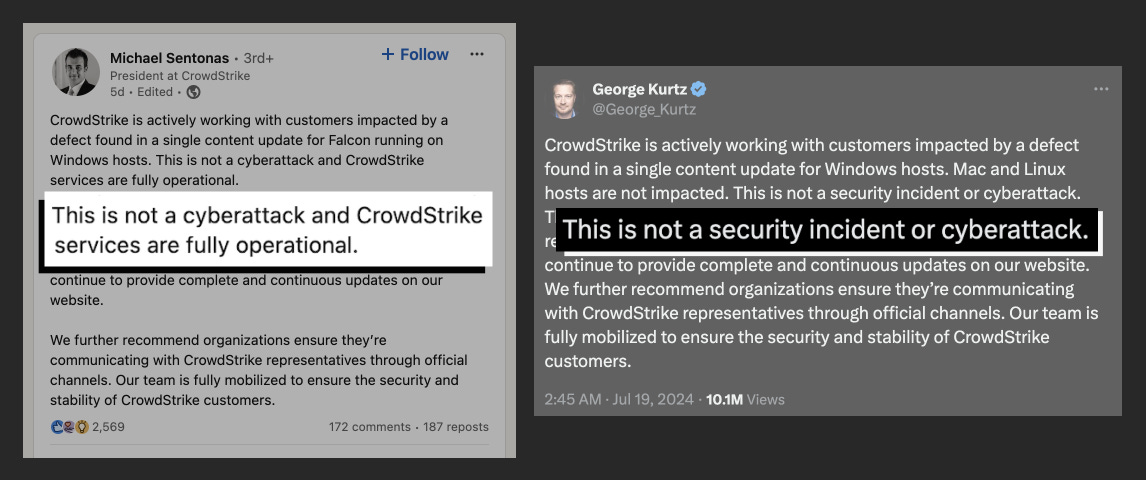
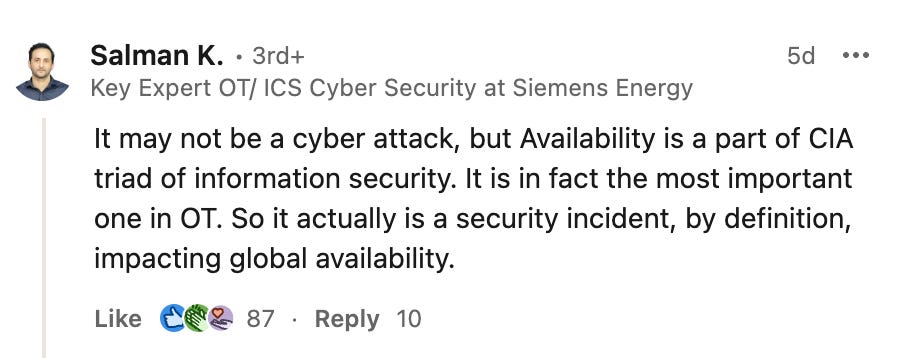
While we learned from every direction that the destruction was not caused by a cyberattack on CrowdStrike, the security industry has been quick to call out the very real cybersecurity impact.
Businesses, banks, hospitals, and airlines were impacted worldwide. The aviation analytics firm Cirium confirmed that 6,855 flights—6.2% of all scheduled flights—were canceled globally on Friday, resulting in stranded flyers, long lines, and, in some cases, handwritten boarding passes. Delta Air Lines was the most reliant on Microsoft and CrowdStrike for its cybersecurity and, as a result, the hardest hit. With over 5000 flights canceled and losses totaling “half a billion dollars in 5 days,” Delta is now openly planning to file a lawsuit, which could be the first of others to come.
Hospitals were forced to cancel operations and appointments due to issues like “digital bottlenecks,” where crucial processes like cleaning, disinfecting, and sterilizing medical devices rely on multiple computers to complete, which were taken offline by the outage.
For US Fortune 500 companies, the outage is now estimated to cost $5.4 billion. So, while this isn’t a malicious attack, it certainly is a cybersecurity incident for all those affected.
But as the affected Windows systems return online, the fallout continues to play out in the form of phishing, malware, and continued recovery.
First, quick hits on the event, timeline, and solutions.
Summary
On Friday, July 19, 2024, CrowdStrike’s Falcon platform released a routine but defective sensor configuration update to Windows systems that changed how Falcon evaluates named pipe execution “to target newly observed, malicious named pipes being used by common C2 frameworks in cyberattacks.”
The update triggered a logic error that led to an immediate Windows system crash. The error has since been identified as a Null Pointer Exception.
The defective update was reverted 78 minutes after it was released on Friday, July 19, 2024.
In this short time, 8.5 million Windows devices were affected, leaving IT and security teams scrambling with only a manual remediation process: boot into safe mode, remove the defective configuration files, and reboot normally. Those with hundreds or thousands of distributed devices—40,000 servers in the case of Delta Air Lines—were hit the hardest, with remediation expected to take days.
Only Windows hosts were impacted, specifically those running sensor version 7.11 and above that were online and received the update within the 78 minutes it was released.
Mac and Linux hosts were not impacted, nor were countries that do not use Windows products, like Russia and China.
CrowdStrike, Microsoft, and practitioners have published remediation guides at the frontline:
CrowdStrike’s official remediation guidance
A Microsoft recovery tool and article on the 0x50 or 0x7E error
A cloud-based remediation strategy CrowdStrike is offering, as shared on Reddit
Notably, the unique nature of the endpoint detection and response (EDR) software—Falcon or otherwise—on Windows exacerbated the chances of complete system failure: to effectively identify advanced malware, EDR requires highly sensitive access to operating system files to launch monitoring tools early in the boot process, as well as permission to make regular automatic updates to keep up with changing attacker tactics. Combined, these factors increase the chances of complete system failure, as in this case.
Phishing, Scams, and Malware
As opportunists, cybercriminals are taking advantage of this urgent and fast-moving crisis to prey on those affected using phishing and scams:
Purported hotfixes for CrowdStrike have delivered HijackLoader, Lumma Stealer, Remcos, and Daolpu malware. These have been paired with fake recovery manuals to appear official and trustworthy.
There’s been an uptick in domain registration referencing CrowdStrike since Friday, with the presumed goal of phishing, scamming, or delivering malware. Some sites have offered fixes in exchange for cryptocurrency payment.
Palestinian hacktivists have attempted to trick Israeli organizations into installing wiper malware on their systems.
Individuals have been targeted with phishing and scams using scenarios like rescheduling missed fights, requesting alternate payment methods, and spoofing legitimate services to steal login information.
The predominant recommendation to combat phishing, scams, and malware is to proactively use official communications channels for remediation and to avoid interacting directly with unsolicited email and text messages.
Final Thoughts
We know attackers routinely take opportunities like large-scale and chaotic events to advance their goals. This reminds us repeatedly that basic security hygiene and training reign supreme, just as phishing and social engineering remain the MVP of attack vectors.
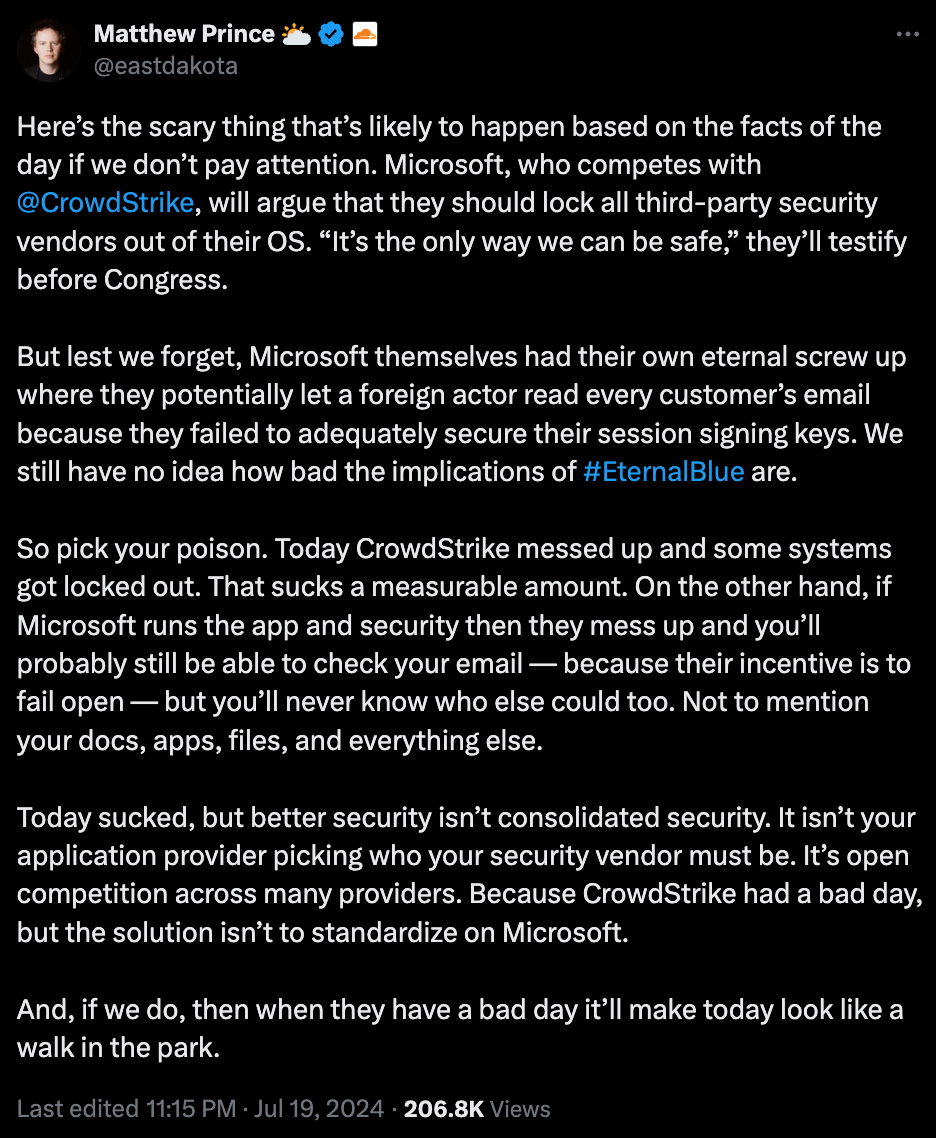
But as we watch the fallout continue, something else comes to mind: the reality that tech giants are truly enormous single points of failure and, likewise, that cybersecurity software is a part of the attack surface it protects. This is surfacing another discussion about security consolidation, or “platformization.” Cloudflare’s Matthew Prince sums up the issue in the following tweet: security incidents will happen, and they are never a good reason to consolidate security and undermine healthy competition within cybersecurity.
What are your thoughts?