An Introduction to Cyber Threat Intelligence (CTI)
Effectively using indicators of compromise and TTPs in SIEM.
Welcome to Detection at Scale, a weekly newsletter for practitioners and leaders running security operations programs. It ranges from detection engineering to cloud infrastructure and includes the latest vulnerabilities and breaches. Enjoy!
Cyber Threat Intelligence (CTI) involves exchanging information to identify malicious actors, active exploits, and ongoing attacks. As defenders, intelligence helps us orient where an attack could come from and how hacker groups take advantage of organizations today. We use the term "Cyber" threat intelligence to differentiate from intelligence governments share about broader security threats related to physical security or geopolitical risks.
Cyber Threat Intelligence (CTI) can improve detection and response capabilities, but if implemented inefficiently, it could result in noise as your security program scales. In this blog post, we'll introduce several best practices and practical techniques for applying CTI to enhance alert quality and add value over time.
Primer
Cyber Threat Intelligence (CTI) is the process of gathering and analyzing data about potential security threats and the actors behind them.
CTI can help proactively detect the early signs of a breach. By sharing reliable and timely indicators, peer organizations can better prepare to protect themselves. For example, if a group of FinTech companies is targeted with the same malware, they can share sample logs, binaries, and external IoCs. Cyber threat intelligence comes in tactical and operational forms, varying slightly.
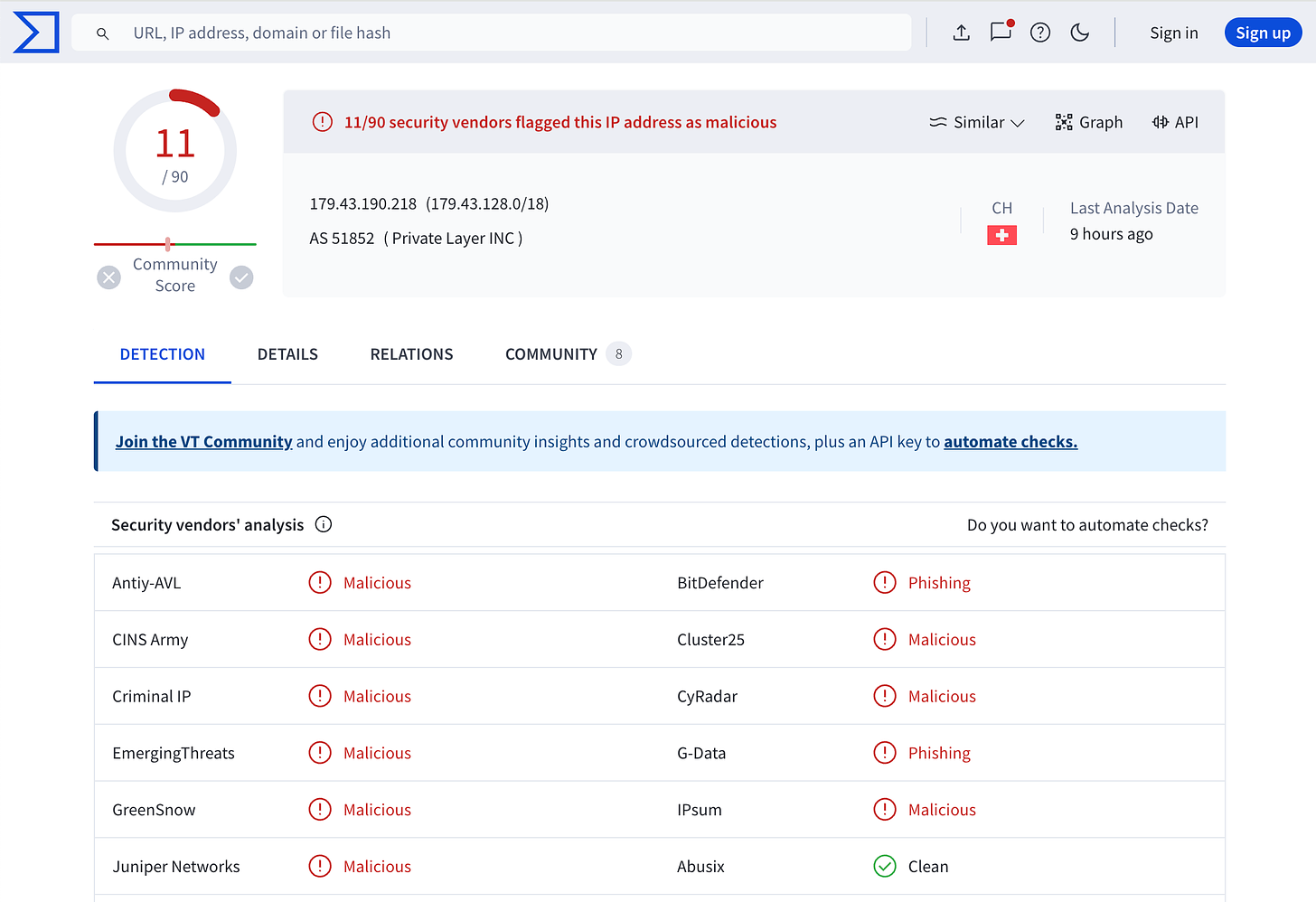
Tactical CTI contains indicators of compromise (IoCs) in the context of attacker tactics and techniques (TTPs). An example is reporting the IP address 179.43.190.218 used for phishing by VirusTotal. Additional information, such as observed processes, remote ports, and network patterns, can also aid in high detection accuracy when declared in SIEM rules. An incident responder's job is to build confidence that a particular behavior is bad or not, and tactical CTI can help gauge the severity of a behavior through various sources.
Aside from indicators and associated behaviors, reports can also contain YARA signatures or file hashes (typically unreliable) for malware identification.
Operational CTI tracks state-sponsored groups and other hacker organizations responsible for publicly reported data breaches, like LAPSU$ and Lazarus Group. These reports focus more on the motivations, intent, and attribution of datasets on the dark web. Keeping up-to-date with each type of threat intel ensures we are prepared for relevant and potential threats at any given time.

In a recent Detection at Scale podcast episode, Jason Craig and I discussed tracking hacker groups like Lapsu$ in addition to threat modeling advice:
Around the time this blog was written, MITRE also published a recount of a recent breach along with relevant behaviors (TTPs) and mitigation tips. While they did not share specific domains, IPs, malware, or specifics of the attack, it provides a great overview and demonstrates a well-orchestrated incident process.
“You can learn a lot from being hacked, and that knowledge can transform an entire industry.” - Advanced Cyber Threats Impact Even the Most Prepared
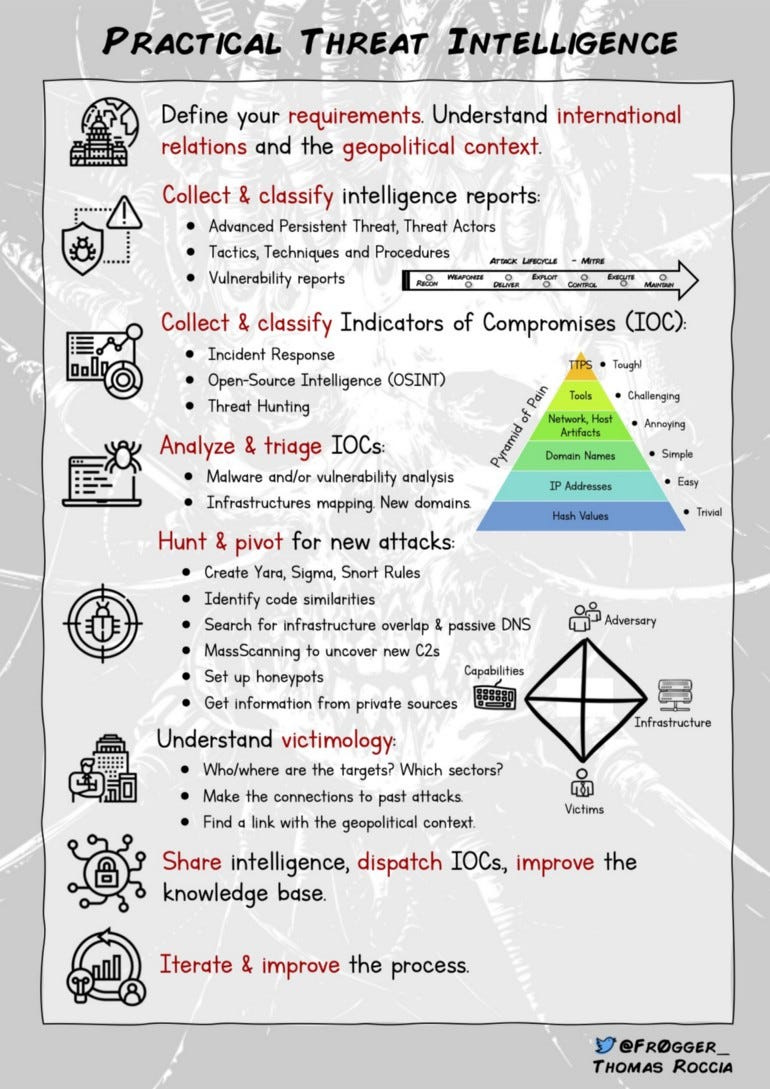
Finally, the graphic below is a great visual for pragmatic threat intel:
Best Practices
Threat Intel often enhances and works in conjunction with Detection and Response programs. In some organizations, however, this function exists independently. If you are just getting started, here are five ways to make the most of your CTI program:
Keep track of indicators from prior incidents
Ensure IoCs and TTPs are used in context
Pick threat feeds relevant to your company
Enrich with CTI during data ingestion
Don’t be afraid to age out IoCs
Tracking Prior Incidents
A core aspect of incident response is Recovery to avoid being breached in the same way multiple times. In addition to augmenting or adding new security controls after an incident, we can keep track of the behaviors and indicators used in the attack. Attacker TTPs can be modeled into SIEM rules to detect how the attackers accessed and took advantage of our systems.
Tracking previous indicators helps defenders quickly react when similar types of attacks occur again in the future. Questions to consider include: Which IPs/domains did we observe, and which kill chain steps were they associated with? Where were the attackers present in our infrastructure?
When we see hits in the future about these indicators or behaviors, they are likely harmful, so we should prioritize investigation and remediation quickly.
We don’t always need to wait until the recovery phase of an incident, though. Dropping indicators into real-time SIEM rules can help pinpoint where to look next and can ensure we eradicate the attackers. While this can be used for quick feedback, taking this approach broadly with CTI is not recommended unless you have high confidence in the indicators.
Using CTI In the Context of Behaviors
It’s very important to apply CTI in the context of attacker behavior.
For example, in this Microsoft blog about Cryptojacking, a list of mining domains is provided in the context of the MITRE “Impact” tactic:
A SIEM rule could be built with the following pseudocode:
domain in miner_list AND dst_port in [443, 5050, 3333] AND is_prod_hostThe more specific, the better. Ideally, defenders could also correlate crypto mining processes launched to the network connections to improve fidelity. If we were to only look for connections to the miner domain list, then any host on the network sending audit logs to the SIEM could trip this alert.
Pairing an IoC with a particular tactic/technique is important because IoCs can be very low-fidelity on their own due to their ephemerality. IoCs, like domains and IPs, can be switched quickly during an attack, but the tactics and behaviors tend to stay consistent. The only time it’s appropriate to be the sole logic for analysis is if there is extremely high confidence in them or if we have seen it in a prior incident, as mentioned in the prior section.
Any SIEM rule should start with intention. What do we need to detect that is relevant to our most critical assets? How would an attacker exploit it? How can we gain more confidence that it’s bad by using CTI? Matching IoCs with behaviors can be an effective way of building more confidence. Check out the post below for a deep dive into Correlation.
Picking Relevant Feeds
CTI comes in many forms and varying levels of quality. Choosing a relevant feed to your industry or technology stack can help enhance the effectiveness of your threat intelligence.
Feeds can range from full reports to free lists of IoCs to commercial TIPs (threat intelligence platforms) that curate intelligence and provide APIs to access them for your SIEM or SOAR. Feeds can also plug directly into network or endpoint sensors in native formats for either detection or sink-holing traffic, a common mitigation technique for making malicious traffic unroutable.
Threat feeds normally have APIs to pull indicators in standard formats that your SIEM can speak to, such as CSV, JSON, or STIX/TAXII. Human-readable reports will also typically wrap domains and IPs with square brackets to avoid auto-hyperlinking and prevent inadvertently communicating with attacker resources (we’ve all done it).
The list below provides a range of feed options, from government-adjacent to commercial to open-source:
Organizations like the National Council of ISACs (by industry)
Open Source projects like MISP or awesome-threat-intelligence
Commercial TIPs like RecordedFuture, Anomali, or Flashpoint
Threat Feeds from Group-IB, CrowdStrike, or Cloudflare
If your organization operates in a highly regulated industry or is often a target, combining several feeds and sources could be beneficial. Also, layering and cross-referencing indicators across feeds can validate IoCs. The more data points, the better! Detection and Response is all about building confidence.
Enriching IoCs in the Pipeline
Finally, to save on historical processing and improve point-in-time analysis, we recommend enriching logs with threat intel as logs are ingested. Due to the dynamic nature of indicators, this can provide a more accurate view of what the world was like at that moment. Implementing this requires hooking your CTI to a lookup table in the SIEM, a fairly standard feature.
Enriching during data ingestion and subsequent analysis automates a previously manual indicator lookup. The downstream SIEM logic can look for certain classifications of IoCs, correlate threat intel with GeoIP information, or compare hits across various users or hosts. CTI can be used as a gate for sending alerts or to adjust severities or destinations for alerts.
This technique only works if threat intelligence can be downloaded in bulk, which may not be efficient in certain cases. If API calls are expensive, they can be made after alerts are created using a SOAR or similar tool.
Using Fresh Data
Due to the dynamic nature of attackers subverting detection, it’s important to put a time limit on CTI. Don’t be afraid to audit and subsequently deprecate old indicators or threat feeds, especially if their fidelity has degraded. As with all detections, a smaller list of reliable, enriched rules with relevant threat intel is better than 100% coverage.
Getting Started
Cyber Threat Intelligence can make you a better defender by keeping up with trends, techniques, and hacker groups that help contextualize and explain incidents or alerts. It’s another tool in the toolbox for understanding the world around us and doing our due diligence when protecting our organizations. It also lets us connect with our peers to share tips and war stories and help during active incidents. As with new programs, we recommend introducing CTI slowly and intentionally, measuring its effectiveness. If you have any tips not covered in the blog post, please comment below! If you found this blog helpful, please subscribe. Thank you!
Additional Reading: